Configuring Guacamole
Introduction
Where we left off, we had a fairly barebones web interface that’s not really doing a whole lot.
Let’s change that.
Setting the admin password
Well first off, guacadmin/guacadmin isn’t a very secure login. Change it to something more appropriate under preferences.
Creating a remote connection
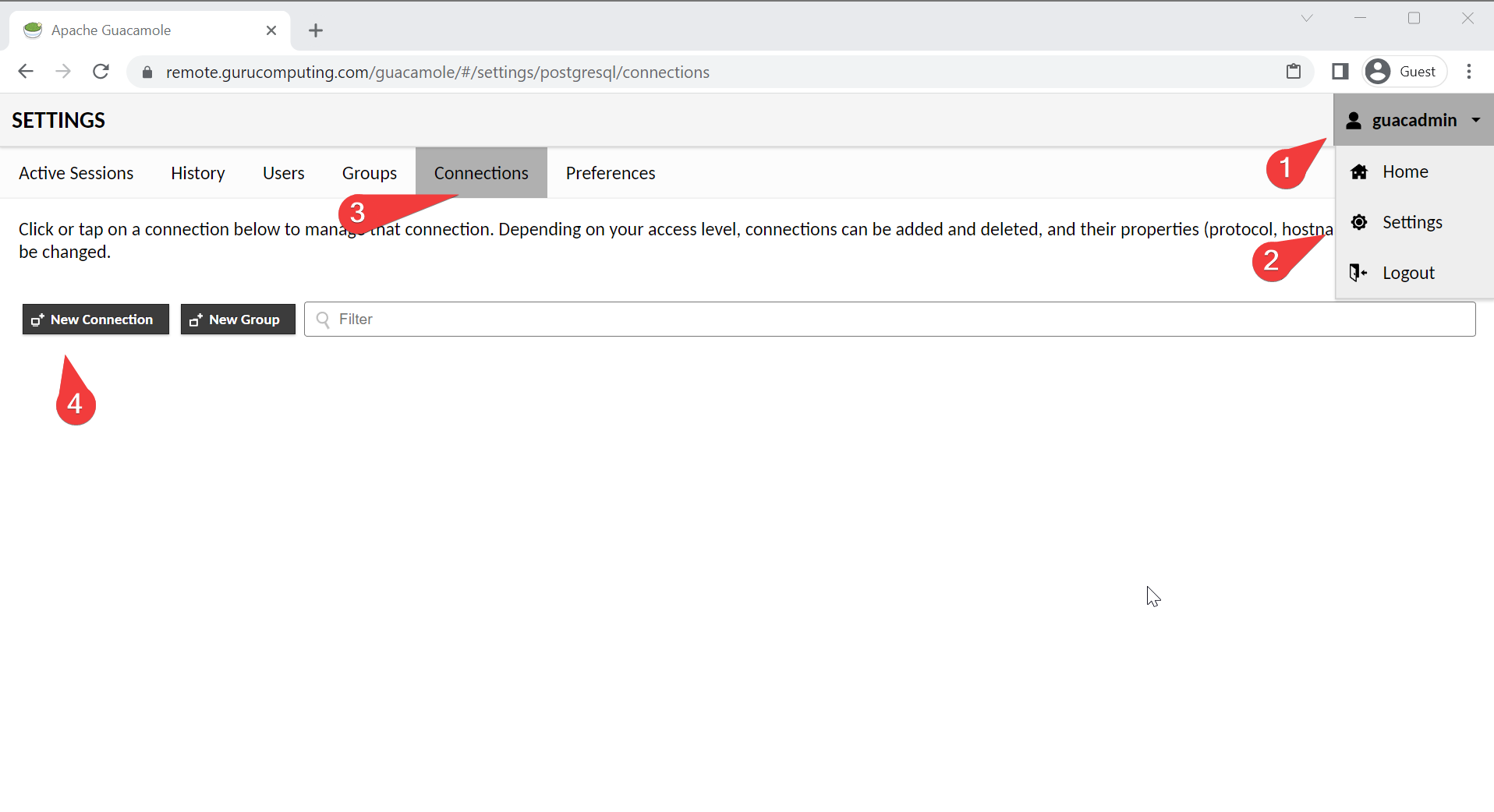
At the core of guacamole, we need to be able to connect directly to servers to administrate them. Well, why not the docker host guacamole is running on? Head to Settings→Connections→New Connection
Info
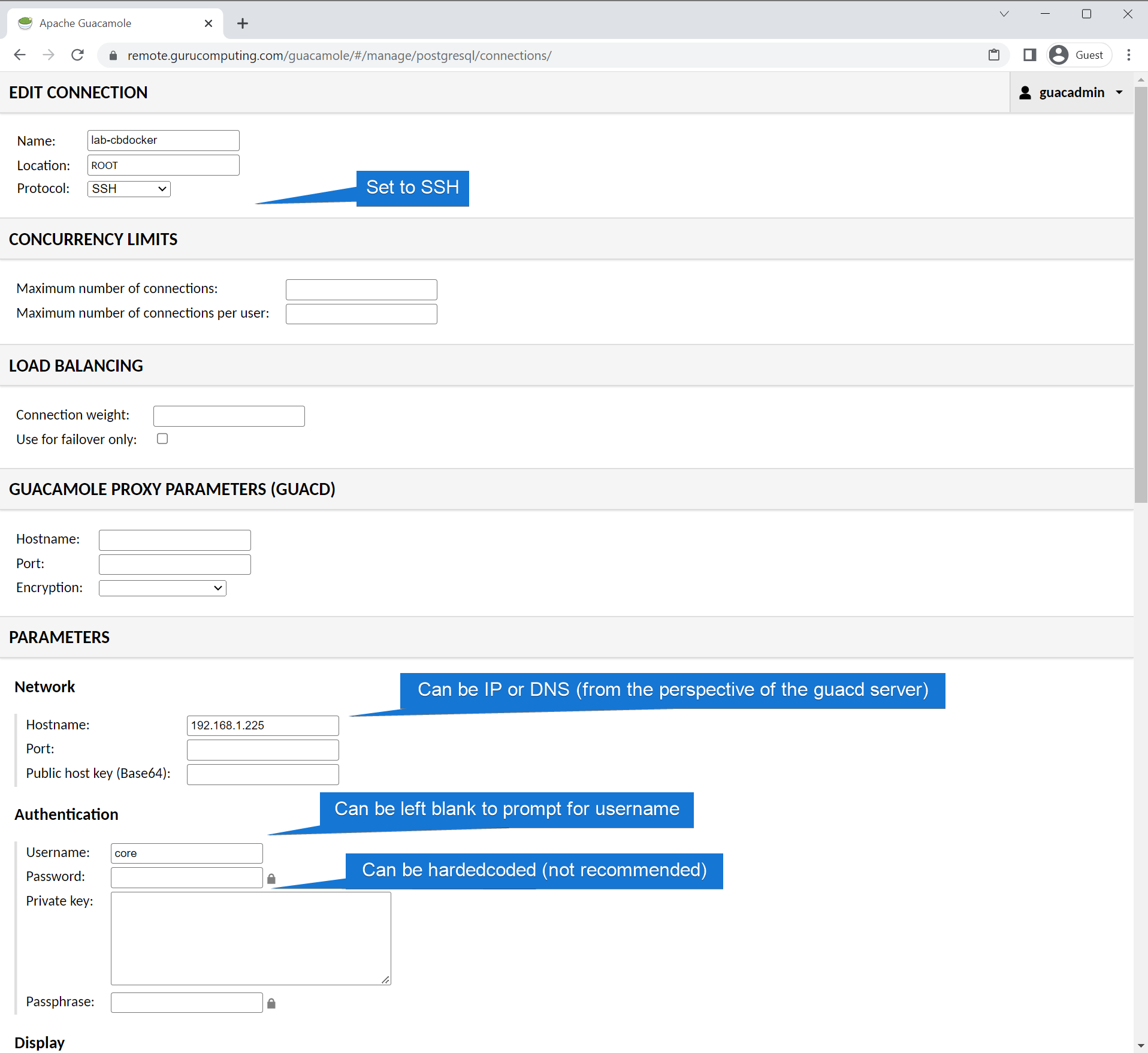
Most distributions disable login via ssh for root (with a password). Either create a dedicated remote user (recommended) or allow root with ssh passwords (not recommended). You can alternatively hard-code a private key into the connection settings, but that also carries some security risk.
- In the new connection, set the name of the connection, the protocol, and the IP of the docker host. There are many more knobs to tweak, but for now we’ll leave most options at their defaults.
- Test the connection out!
Cool, we’re monitoring the guacamole container in guacamole via ssh. A bit of inception vibes, but still cool!
RDP Connection
Alright, let’s try this again with RDP. We have a handy dandy server 2022 box setup for this purpose.

Again there are a lot of settings we can pursue, but most can be left at default. At minimum I suggest enabling ClearType:

And with that done, let’s test!
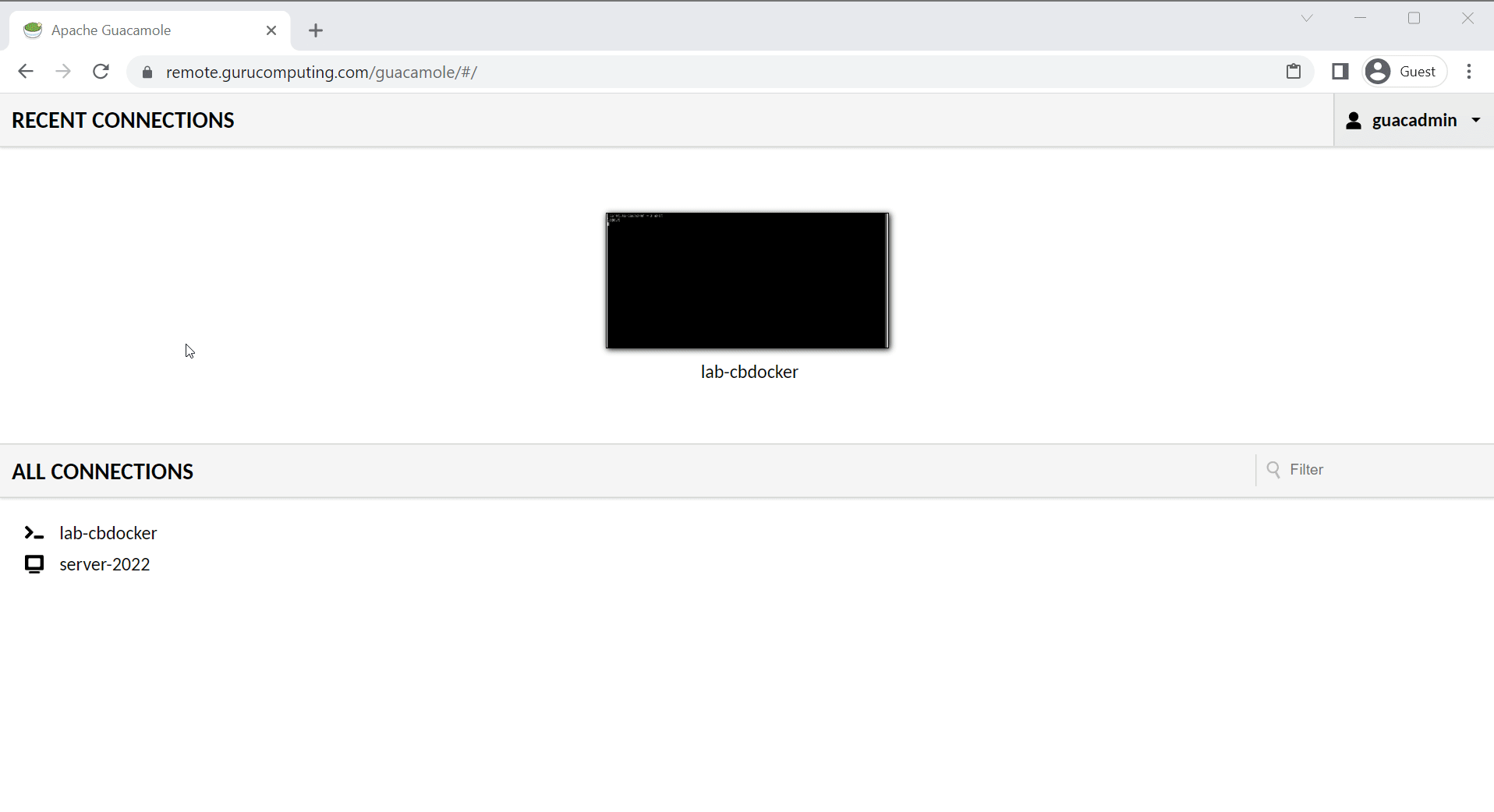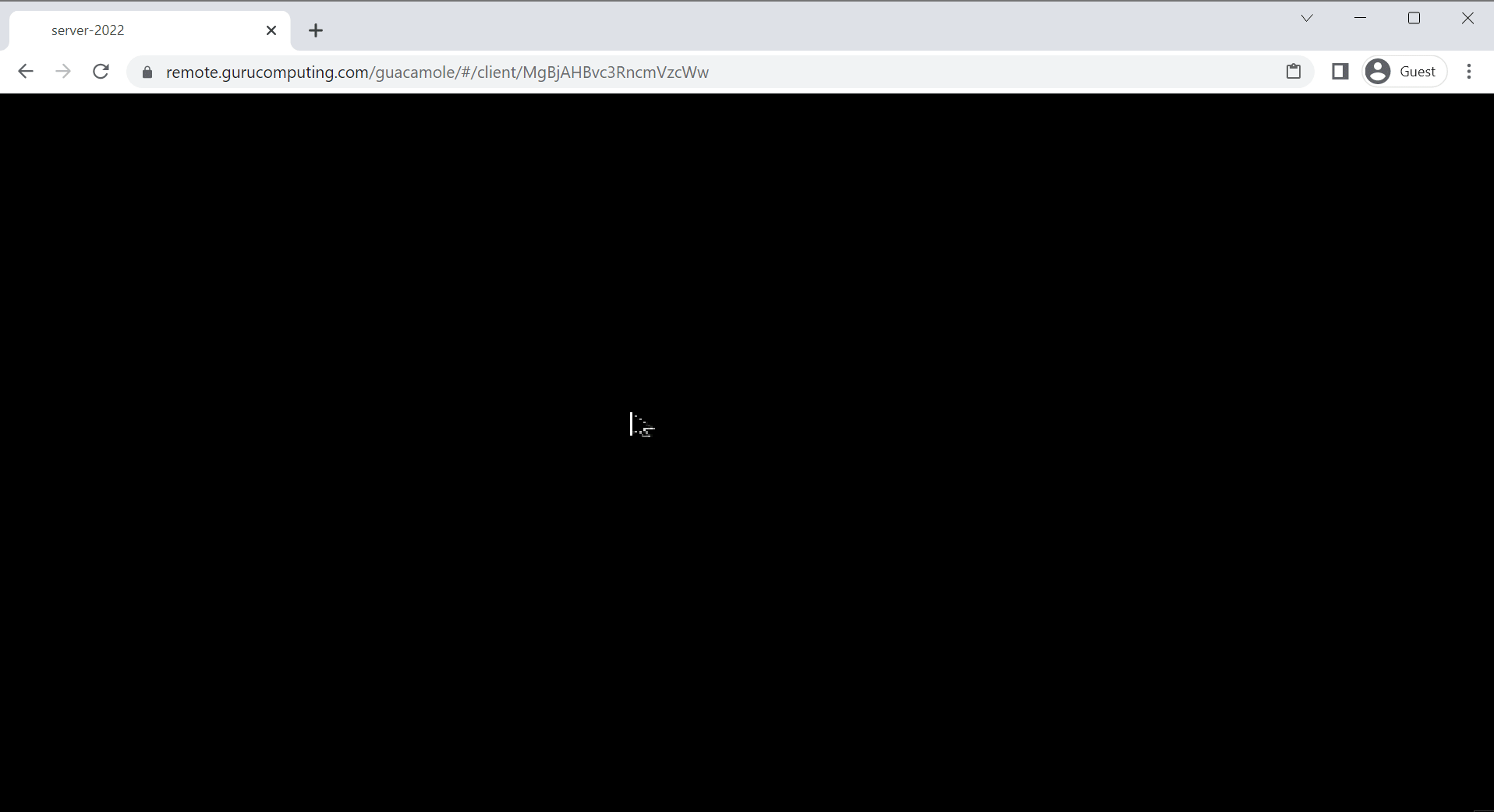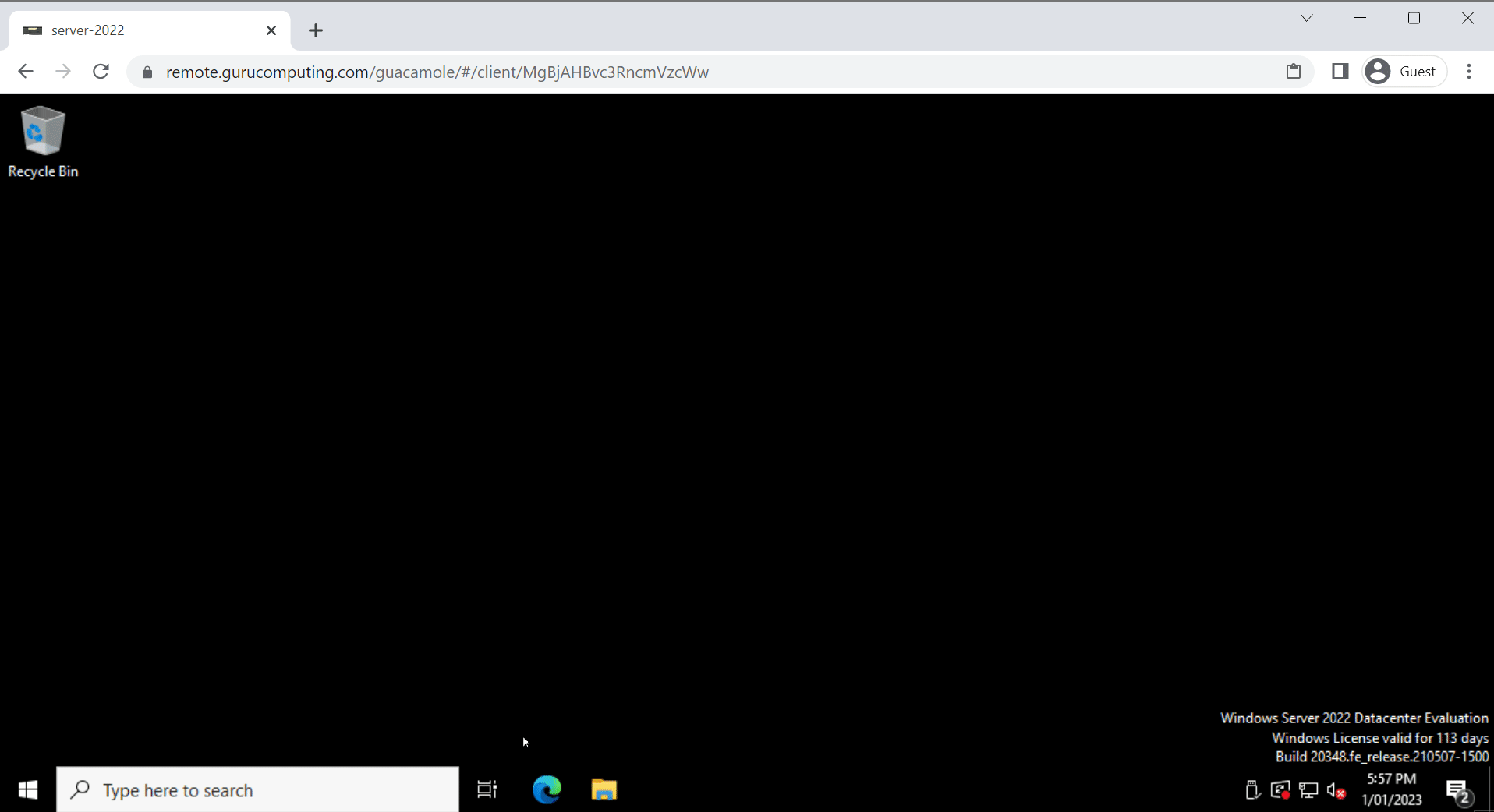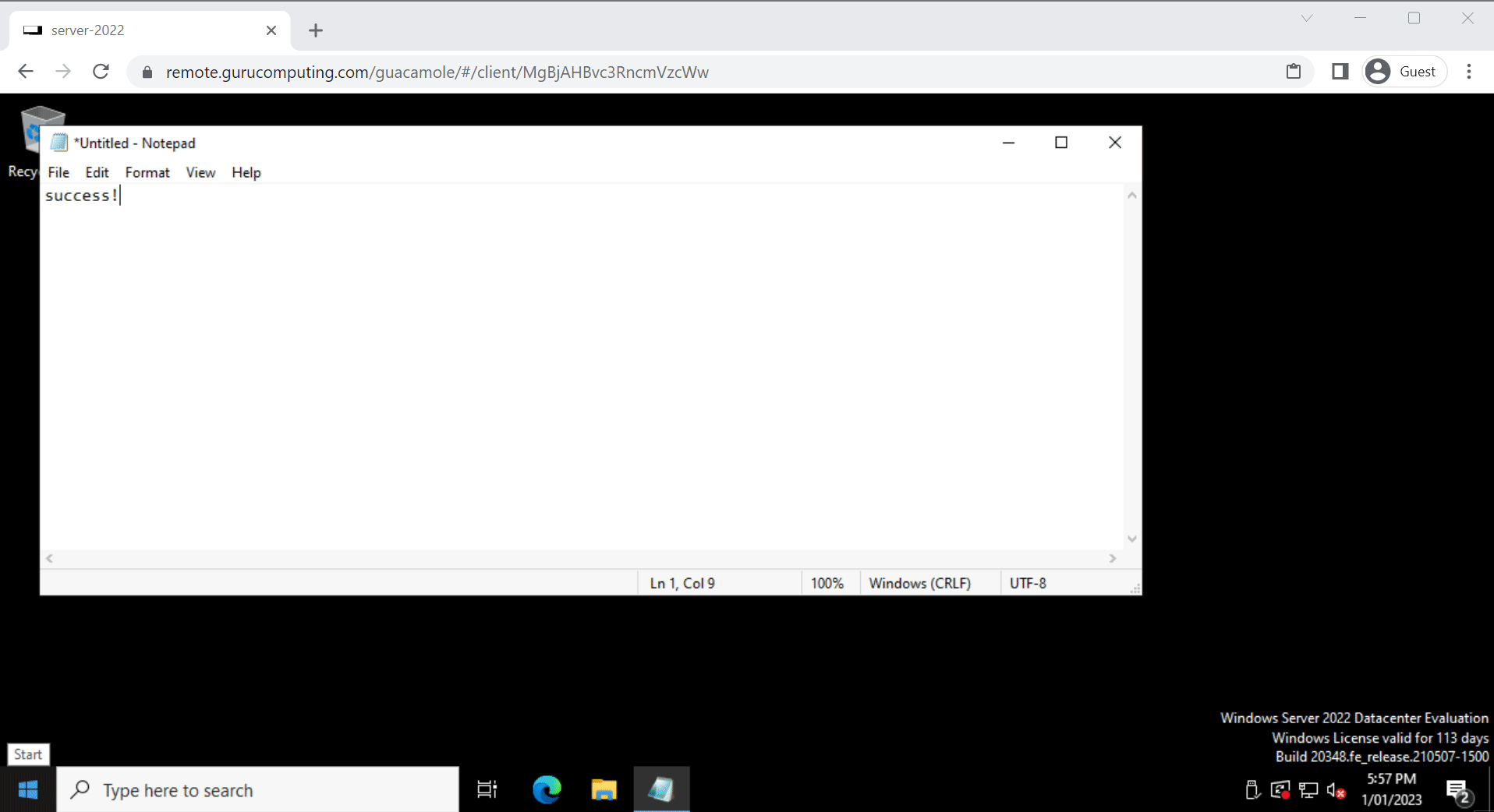
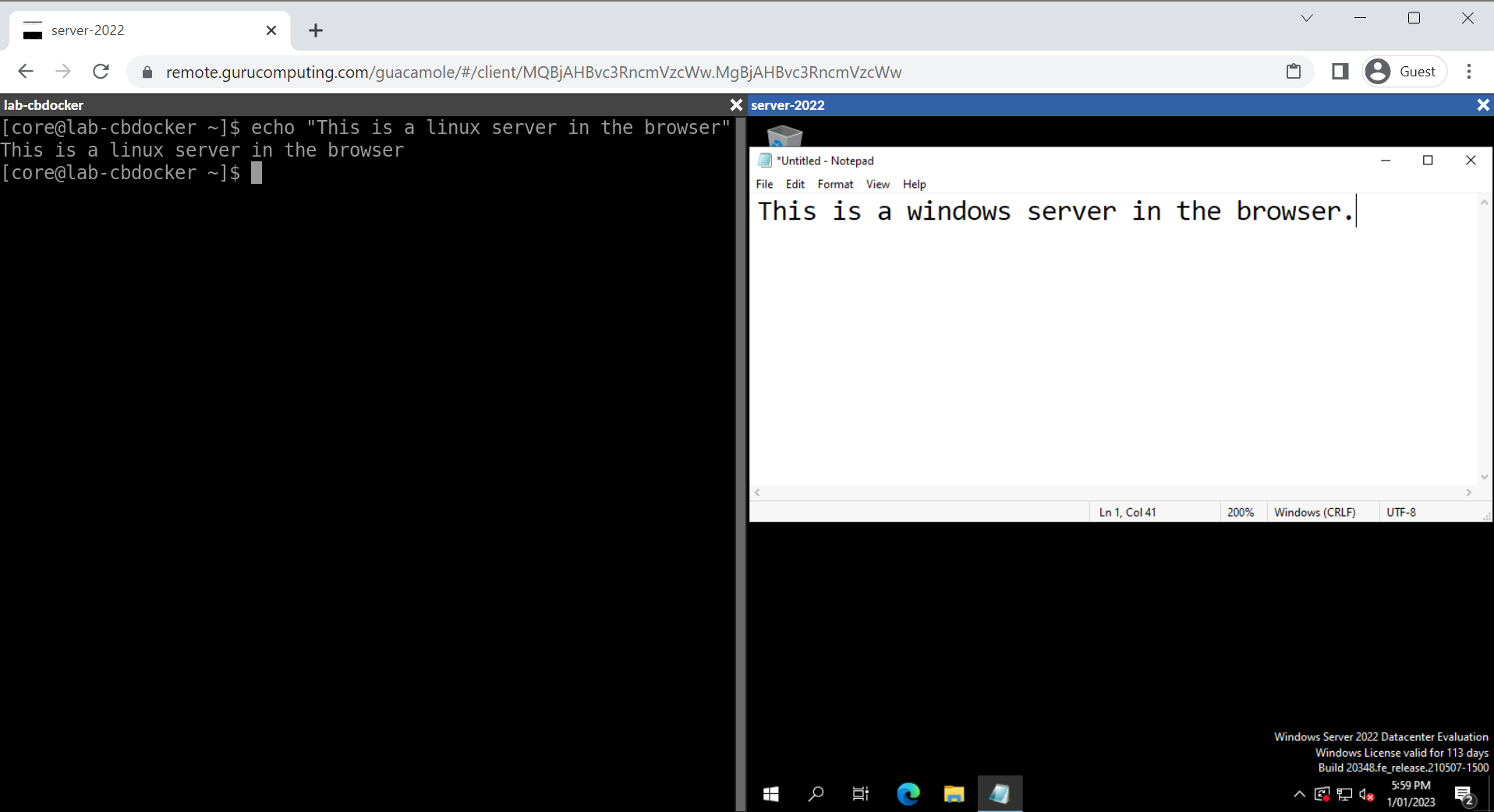
Woohoo! One of the coolest features about Guacamole is also the ability to seamlessly switch between multiple servers. Heck, you can even tile them and work on multiple servers simultaneously:
Multi-factor Authentication
One of the big selling points for setting all this up is enabling multi-factor authentication for administrative access. Aside from being a mandatory requirement for many businesses, now that we’re in the browser it’s quite trivial.
The normal recommendation would be to set up SSO (see my keycloak guide here) and enable SSO. In fact, we will be doing that in the very next article. However, Guacamole also has a built in capability for multi-factor. Let’s demonstrate that now.
- First we need to install a plugin. For 1.4.0 you can find the plugins here. The one we care about is the one for TOTP
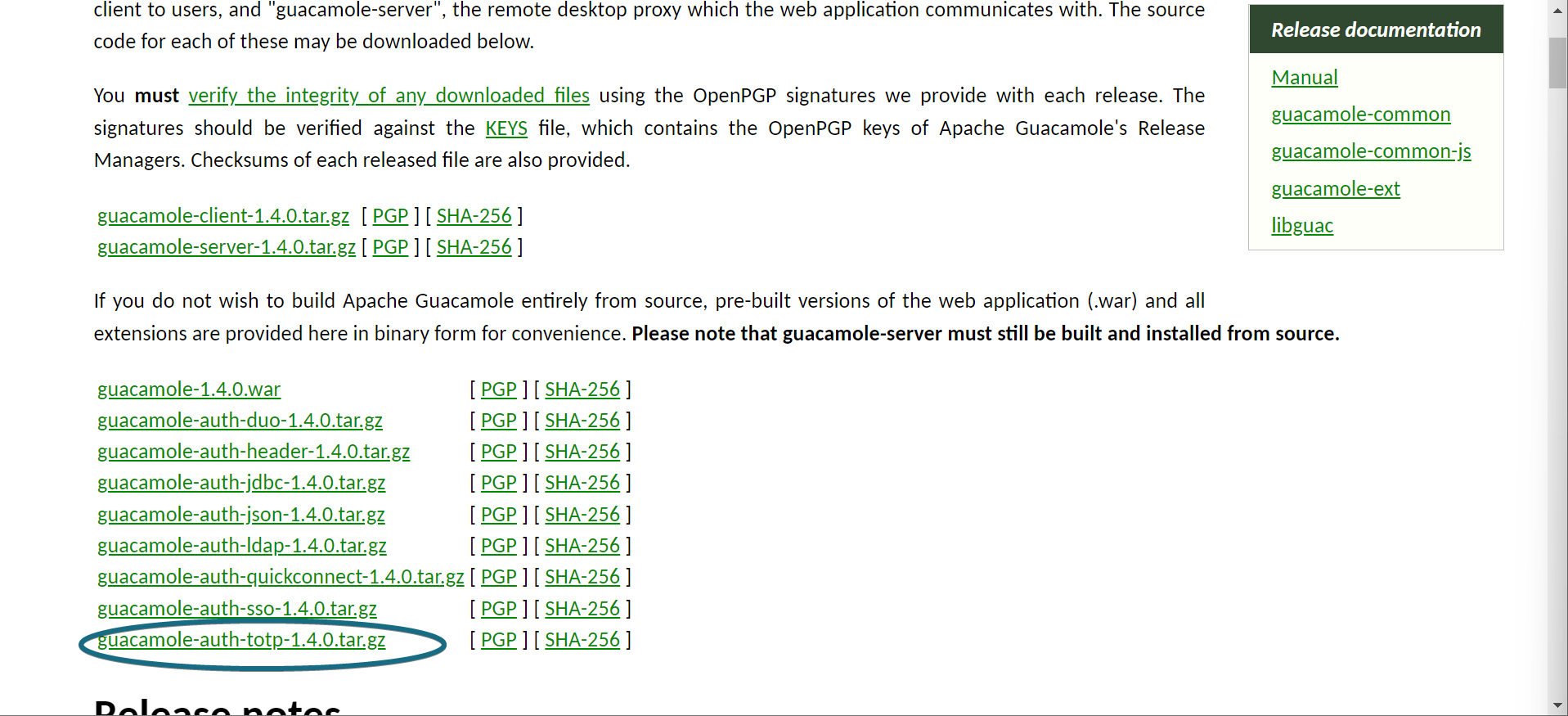
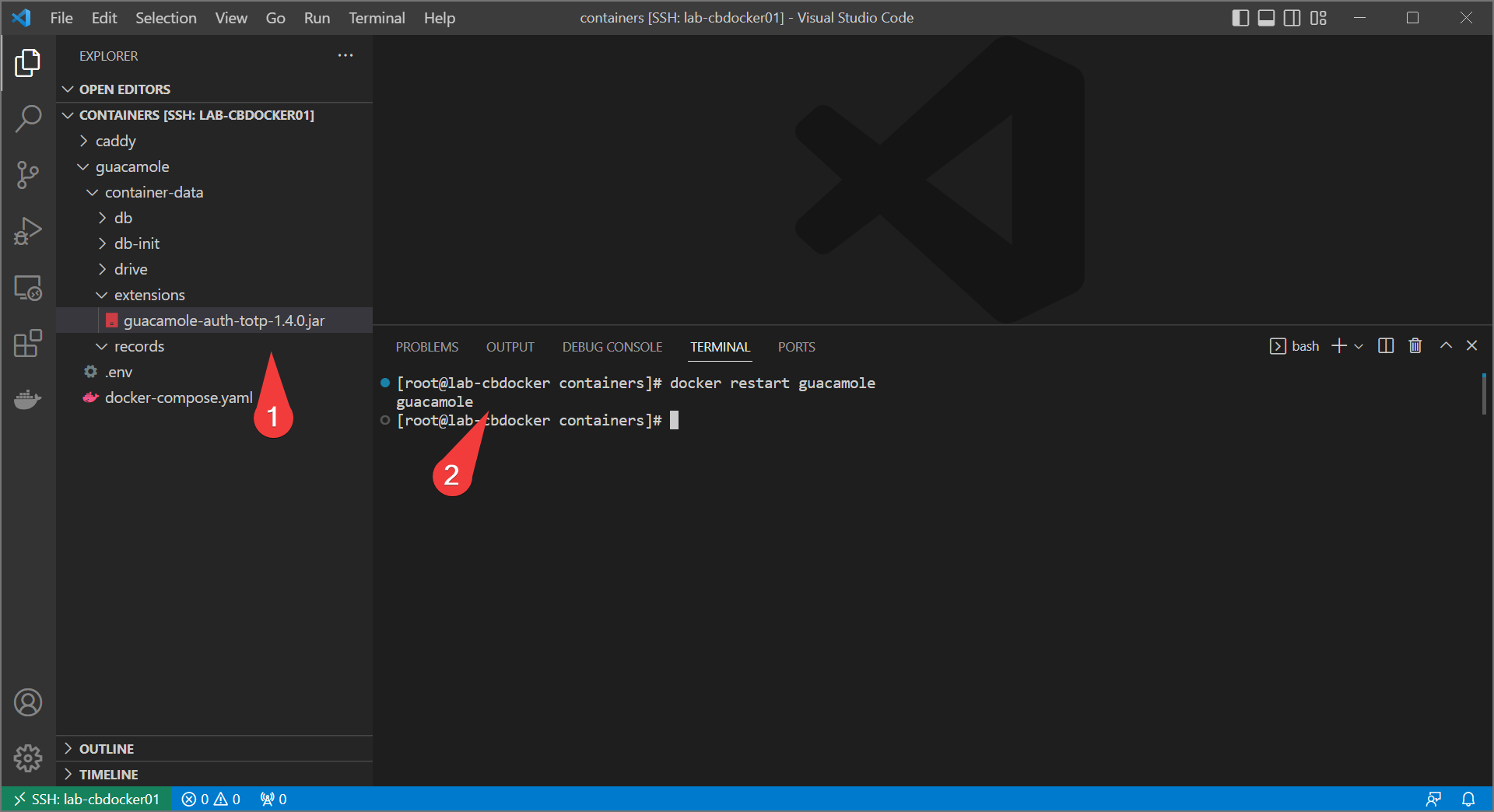
- Download/extract the TOTP plugin and place
guacamole-auth-totp-1.4.0.jarin<your container volumes>/guacamole/container-data/extensions. Restart guacamole
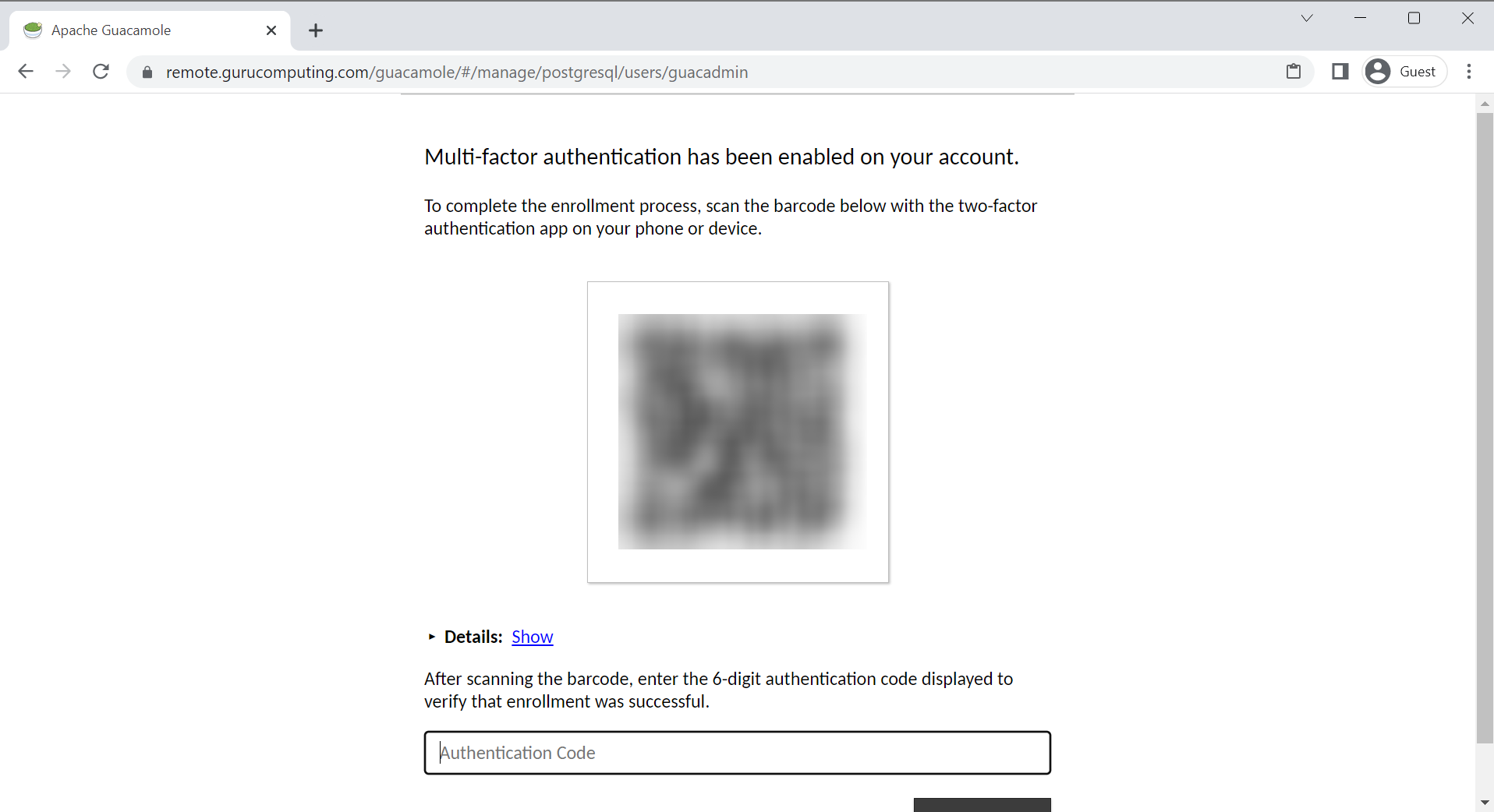
- Next time you log in, you should automatically be prompted to enroll a TOTP token (present in most authenticators, like microsoft authenticator or bitwarden) to enable MFA!
Moving On
There’s a lot of features within guacamole that we haven’t touched on, but the core functionality is now present and ready to use. However, for a business installation we probably aren’t going to be using local accounts at all. Let’s cover that next with Guacamole SSO Integration.