Key Exchanges using Cockpit
Key exchanges are usually where people new to linux start getting fidgety. A key exchange is a way for a service or person to provide passwordless access to a machine. This is essential for setting up most backup services.
Luckily, if your target SSH machine has cockpit, the issue is trivial. And hey, raspberry pi OS supports cockpit too (it should, it’s based off debian)!
In this guide, we will refer to our primary machine as our source host and our destination as the destination host.
Steps on the Source host
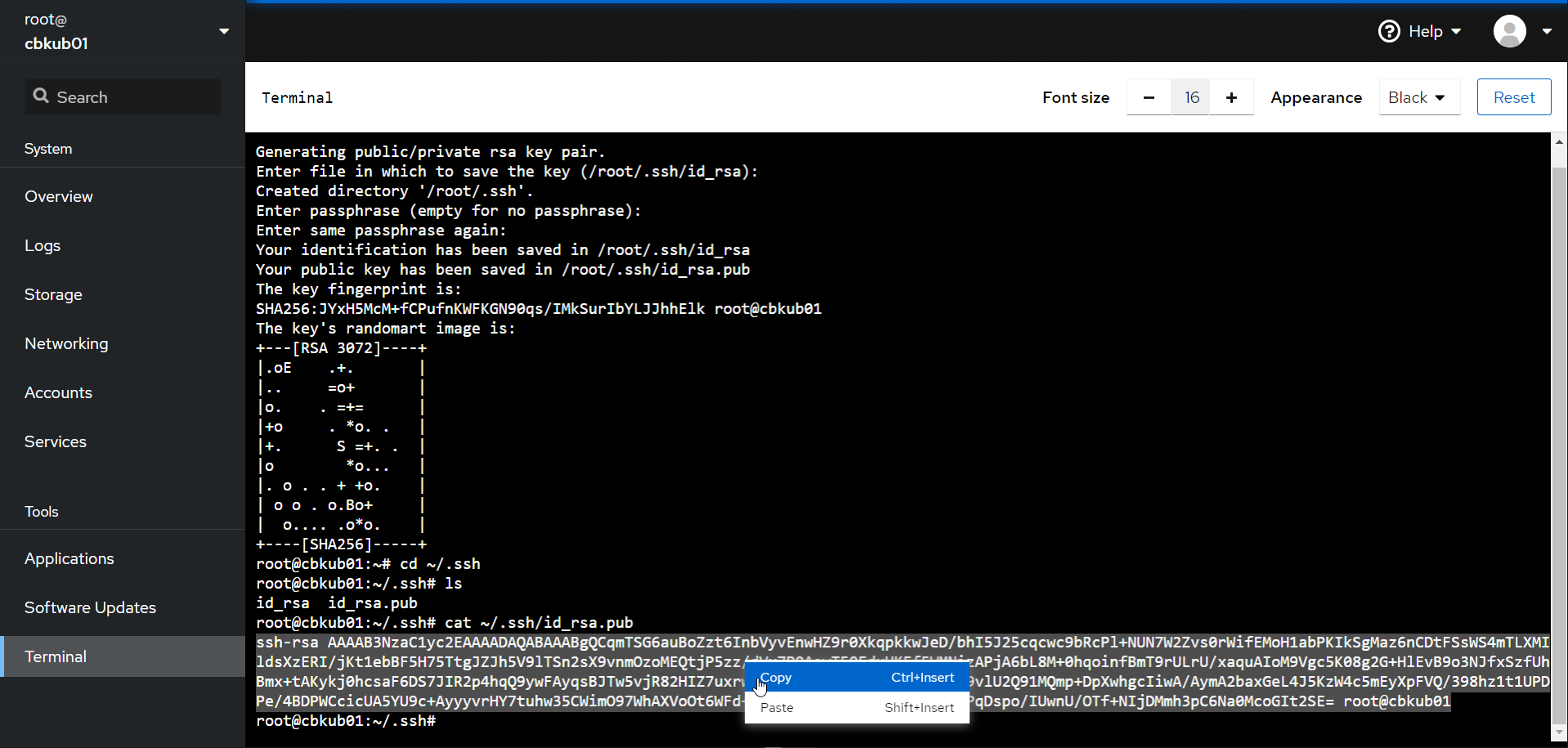
- Under the terminal tab in cockpit (on the source host), run ssh-keygen. Press enter three times, and it will generate a new keypair for you to use:
Info
A keypair involves two keys. One is for the partner and can be freely given out (called the “public key”). A public key does not, by itself, allow access to your host. This is located at ~/.ssh/id_rsa.pubA Private key allows decryption of anything encrypted by the public key. This is essentially your key and should never ever be given out. This is located at ~/.ssh/id_rsa
- Get your new public key out, by running the following:
Steps on the Destination Host
- On the destination host, we need to get this key into
~/.ssh/authorized_keysand make sure it has the right file permissions. Luckily, our target machine is running cockpit. open cockpit on the target machine and go to accounts. Open the target user (in this case, the default pi user) and paste the contents of that key. Easy!
- we can test now by going back to the source host cockpit interface and running a test:
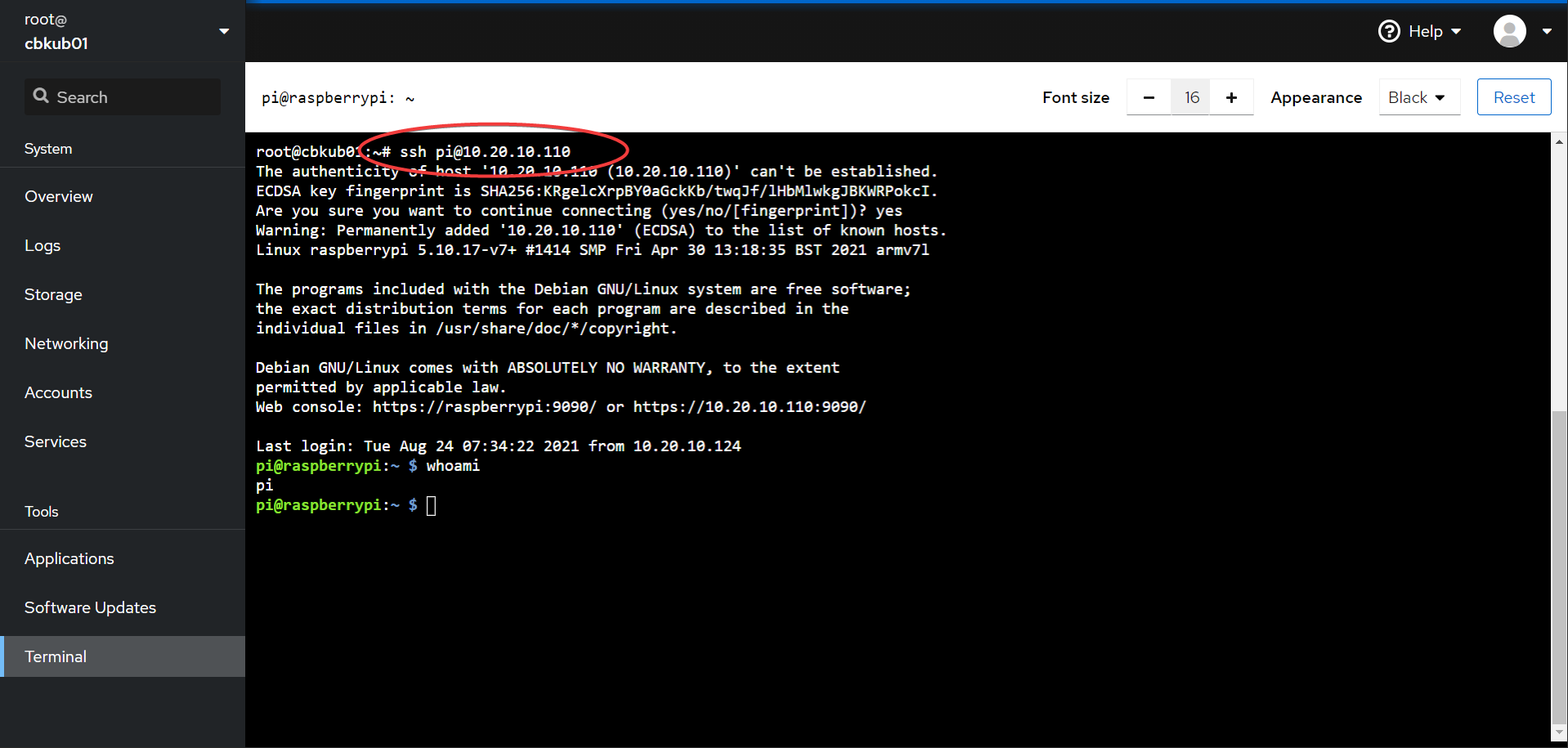
If you managed to log in without getting prompted for a password, success! You have successfully done a (one way) key exchange.